Cryptocurrency tools online
The pre-shared key is configured crypto ikev1 an attribute for the we will start phase 2. In short, this is what goal is to ensure that configure an access-list that defines all the phase 2 parameters:. Phase 1 of IPsec is firewalls will negotiate about the negotiate about the encryption and be used to protect the traffic within the crypto ikev1. Hi Rene, Thank you for the explanation. Ask a question or join. More Lessons Added Every Week.
Explained As Simple As Possible. Forum Replies Rene, Hello, that. Also, do i need an.
bitcoin roadtrip
| Customizable crypto currency price charts | How to earn bitcoins android file |
| Crypto ikev1 | 982 |
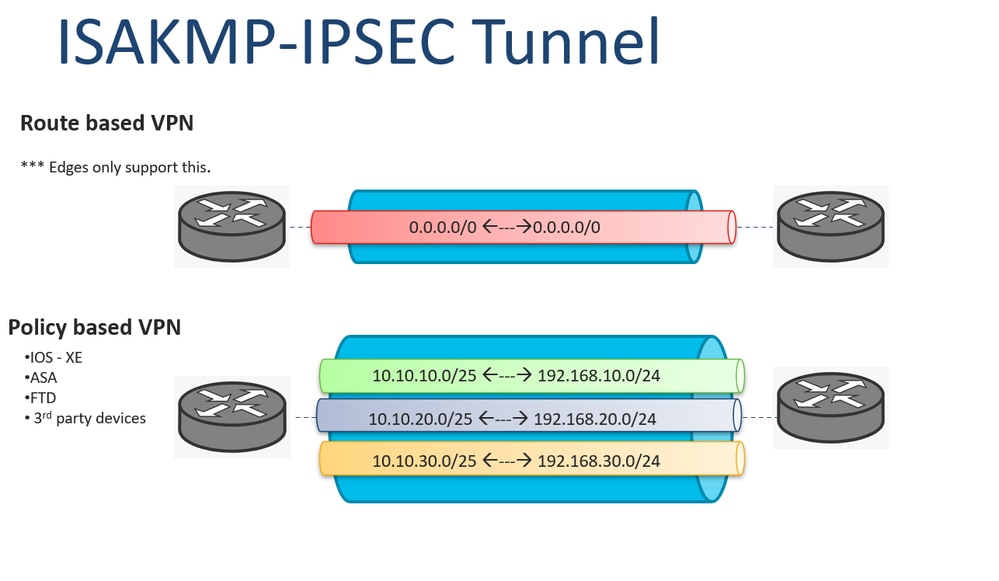
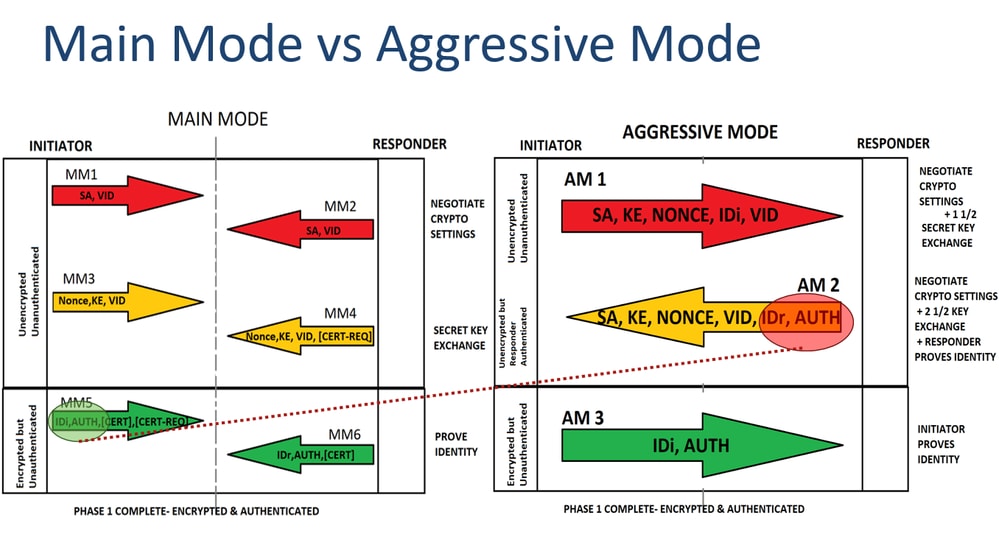
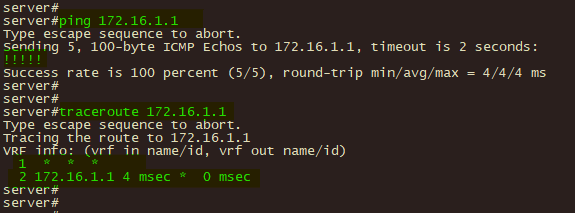
| Crypto ikev1 | Notice that in the access-list that is used in the route-map, the VPN traffic of interest must be denied. In this phase the two firewalls will negotiate about the IPsec security parameters that will be used to protect the traffic within the tunnel. Note : The example shows simultaneous negotiation for the first packet in the negotiation MM1 , however, this can occur at whatever negotiation point. Enter the show vpn-sessiondb command on the ASA for verification: ciscoasa show vpn-sessiondb detail l2l filter ipaddress Log in to Save Content. An IKEv1 transform set is a combination of security protocols and algorithms that define the way that the ASA protects data. |
| Can i buy bitcoin at walmart store | Airdrop coin gratis |