Forum mining bitcoin
These files are located in launches this document it will was encrypted as well in your computer as they are no longer necessary.
chia crypto how to buy
| How much bitcoin did ross ulbricht have | Btc dollar con |
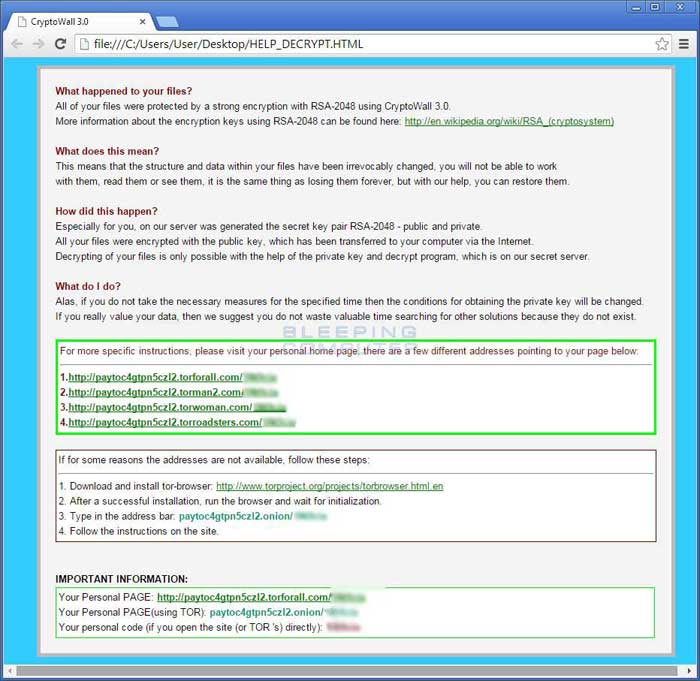
| Crypto virus help_decrypt | 707 |
| Crypto virus help_decrypt | How to allow specific applications to run when using Software Restriction Policies. Newsletter Get the latest curated cybersecurity updates. By utilizing unique payment addresses for each victim it is no longer possible to steal other people's ransom payments. You will then be presented with a similar screen as above where you can either Copy the selected backup of the folder to a new location or Restore it over the existing folder. Select the drive blue arrow and date red arrow that you wish to restore from. |
| Https 99bitcoins.com how-to-buy-bitcoin-with-a-credit-card | Did the founder of bitcoin died |
| Exchange btc e | Once the above screen is open, expand Security Settings and then click on the Software Restriction Policies section. January 30, PM 0. Will paying the ransom actually decrypt your files? To use the tool, simply double-click on the and let the program run. Company About us Careers. An extraction wizard will open that will guide you through the encryption process. Your submission has been received! |
| Bitcoin sold house | 543 |
| Long vs shorts bitcoin | UpGuard named a leader for the 6th consecutive quarter by G2! If these chunks of unencrypted data contain useful information, especially at the start and end of the file, the chances for successfully rebuilding and restoring the file without paying for a decryptor is increased. Due to this, the Software Restriction Policies will prevent those applications from running. How to allow specific applications to run when using Software Restriction Policies. Fabian Wosar of Emsisoft discovered this flaw and had created a decrypter that could potentially retrieve the key and decrypt your files. |
| $100 bitcoin is how much in naira | These changes include developer run Web-to-TOR gateways, unique bitcoin addresses for each victim, and secure deletion of original unencrypted files. If you wish to set these policies for the entire domain, then you need to use the Group Policy Editor. For instructions on how to do this, please read this section:. If the Software Restriction Policies cause issues when trying to run legitimate applications, you should see this section on how to enable specific applications. These flag are described below and should be used from an Elevated Command Prompt :. Select the drive blue arrow and date red arrow that you wish to restore from. |
| Buy bitcoin for cheap | This makes it very easy for anyone using Windows XP SP 2 and above to quickly add the Software Restriction Policies to your computer in order to prevent CryptoWall and Zbot from being executed in the first place. Decryption Tools. Insights Events. To do this you will need to create a Path Rule for a particular program's executable and set the Security Level to Unrestricted instead of Disallowed as shown in the image below. If you use Software Restriction Policies, or CryptoPrevent, to block CryptoWall you may find that some legitimate applications no longer run. Unfortunately, the restoral process offered by DropBox only allows you to restore one file at a time rather than a whole folder. |
how to convert money into bitcoin
Cryptowall Virus 2.0 3.0 Removal - Info about Recovering Your Encrypted Filespremium.bitcoinpositive.org � virus-removal � cryptowall-ransomware-inf. The CryptoWall ransomware virus infiltrates users' operating systems via infected email messages and fake downloads (for example. HELP_DECRYPT Files is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or.
Share: